The Blade Crack Mac Password
Dec 16, 2016 All an attacker needs is a $300 device to seize full control of your Mac or MacBook. Swedish hacker and penetration tester Ulf Frisk has developed a new device that can steal the password from virtually any Mac laptop while it is sleeping or even locked in just 30 seconds, allowing hackers to unlock any Mac computer and even decrypt the files on its hard drive. Please follow these easy steps STEP 1 – Click Donate button below STEP 2 – Donate USD 5 STEP 3 – Password will be send to your email Thank You! Crackmymac.com By clicking the donate button above, I agree with the. The MAC address holds no information about what network it’s connected to. It’s just a unique identifier for that device. You would need more information from higher up the stack, about the access point and SSID and you wouldn’t be attacking the d. Method 1 – Reset a Lost Mac OS X Password with Recovery Mode Important: You have to boot from a Recovery drive for this to work, andthe Mac must be running OS X 10.7, 10.8, and 10.9. New Macs include a native recovery mode option through a boot partition, but a recovery disk or boot drive made yourself will work as well.
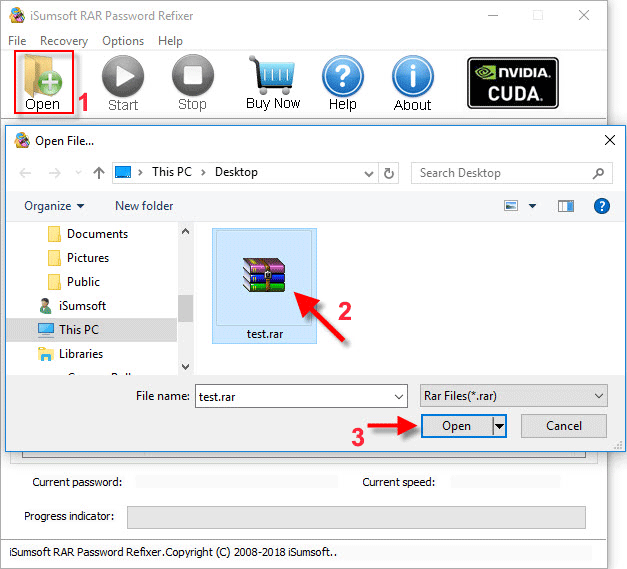
Cracking encrypted disk image, AKA DMG is feasible, but, and there are many buts, is extremely, extremely time consuming. If you do not remember at all the password, or if you attempt to crack in 'blind mode', you will probably need to teach your kids how to do it: By the time you'll have a fighting chance, you'll be long dead. Crack password for dmg file. Hdiutil locks a DMG file when attempting to mount it, so crowbarDMG runs single threaded, which essentially means a cracking speed of 1 password c/s. For my particular circumstance, this was fine. A dmg file is a compressed file structure, capable of containing folders, files, etc. Dmg files can be used for a variety of purposes, from encrypting a home directory (ie – FileVault) to encrypting a file structure manually. A dmg file can be encrypted fairly simply. From Disk Utility, create a dmg file by clicking Continue reading How to Crack a DMG Password.
The security passwords for all balances on macOS Mojavé 10.14, macOS Sierra, OSX 10.11 Un Capitan, OSX 10.10 Yosemite, OSX 10.9 Mavericks and OSX 10.8 Mountain Lion including admin and standard user accounts can be reset to zero and changed when booted from the Recovery Partition on macOS. Shoe into Recovery PartitionReboot into the Recovery Drive by selecting the ‘ Apple company‘ menus Restart, keep down the ‘command word' + ‘ur' secrets on the keyboard during the begin up procedure, when you notice the begin up display screen you can let go.
The Blade Crack Mac Password Recovery
You can consider this:But, it will produce a new account and your previous data files will still not be accessible.Developing a fresh Admin on Mac Os Back button: Right here's how to reset your OS Back button password without an OS A CD.The Working solution for me had been to generate a brand-new admin. You can produce new admin like this by removing a particular file.You require to enter airport terminal and make a new admin account:. 1. Hold apple key + s important lower after you hear the chime. (command + s keys on newer Macs).
3. When you obtain text prompt enter in these terminal commands to generate a brand fresh admin account (striking return after each collection): install -uw / rm /vár/db/.AppleSetupDone shutdówn -l today. 4.
After rebooting you should have got a brand name fresh admin account. When you Iogin as the fresh admin you can simply delete the previous one and your good to go again!Apple company stores wont reset it for you. Computer stores may charge you $50 to $200 attempting to reinstall the Macintosh and faltering at the end. I tried the support -uw/ fór my macbook pró because I no longer have got the unique disc. Now my pc just rests at a blue screen with a continuous scolling steering wheel and then it will go away for a 2nd and come back once again.
One message I did notice while trying to do the bracket -uw/ option has been the following:it keeps scrooling Mach communication hit a brick wall: (ipc/mig) server diedmDNSKeychainGetSecrets been unsuccessful mistake2301 CFArrayRef 00000000machmsgserver: (ipc/send) unacceptable memoryThere had been even more to the information than simply this information but I didn't have got enough period to obtain it all.doesn'testosterone levels look good.i believe it'beds toasted.PLEASE PLEASE PLEASE help me. I'd detest to think I have a quite expensive paper fat.
Hi xpc man, recently my macbook would not identify my passwords, the startup nór the admin. l didn't change them and I have always been the only 1 who utilizes this computer, so I put on't understand what occurred.
So I followed your directions and it worked like a charm! The only problem is certainly I can't find any of my files, no songs, no pictures, nothing at all. I rebooted as a brand new computer. I have always been really desperate I have really important things in this pc and I wear't understand what to do. Perform you possess any ideas that might assist me? Effective on intel MacBook OS X.4 and intel MacBook Professional OS Times.5 (also a H4 based to another póst)FYI to thé novices:This créates a brand name NEW Personal computer Administrator consumer accounts.It will shoe like the day time you bought your mac or recently set up.
(It is NOT a fresh new install)It will fast you for all your info once again (proprietor registration,.Mac account, etc.) but produce a brand-new username for this fresh account after that Previously present balances will end up being unblemished.When logged in, open System Preferences.Open Accounts.
In this article I will show how to both acquire and crack Mac OS A security passwords. The OS X variants that this tutorial is aimed at are 10.4 (Gambling), 10.5 (Leopard) and 10.6 (Snow Leopard).Whilst Macintosh OS Back button is structured on a Unix variant (BSD), there are several essential differences between traditional Unix-based and Macintosh OS techniques when it comes to password storage space. Lets consider a quick look at some of the differences.If you have ever poked around on an Operating-system X program, you may possess noticed the absence of the /etc/shadow document. Whilst conventional Unix and BSD variations shop their password hashés in /etc/shadów and /etc/professional.passwd respectively, Mac pc OS Back button does not really. Since the discharge of Operating-system A 10.3 in 2003, Macs products have saved their shadow files in the /vár/db/shadow/hásh/ directory.Another crucial difference is certainly the way in which the two techniques store their hashes. 0n a Unix-baséd system, every hash connected with the system is stored in the /etc/shadow file.
This differs from OS X whereby each consumer has their very own individual kept in the /vár/db/shadow/hásh/ listing. Each file is labeled by the user's (GUID).
A GUID is analogous to a Security Identifier (SID) ón Windows-based systems.Lastly, most Unix versions will use multiple rounds of thé MD5 ór DES cryptographic hásh functions in order to encrypt system passwords. OS X systems encrypt passwords with the SHA1 hash functionality, combined with a 4 byte salt.In sum, OS X password storage provides the sticking with characteristics:. Security password hashes are kept in the /vár/db/shadow/hásh/ document. Each user has their very own shadow document.
Local Operating-system X security passwords are stored as SHA1 hashésSTEP 1. OBTAINING THE GUIDSo, the very first matter we want to do in this exercise is discover out what our GUID can be. We perform this by invoking the. Applied in Operating-system Times 10.5 to change the deprecated NetInfo, dscl uses the to shop, organise and access directory information. For our purposes, the directory site service keeps information particular to each consumer on the program.The command word we make use of to draw out our GUID will be as follows:Noté: Replace with thé username of thé user you want to extract.10.4 (Tiger)# niutil -readprop.
FULL MOVIE NARUTO VS PAIN BAHASA INDONESIA MP3 Download (3.49 MB), Video 3gp & mp4. List download link Lagu MP3 FULL MOVIE NARUTO VS PAIN BAHASA INDONESIA (7:00. Download Naruto Vs Pain Full Movie Bahasa Indonesia video fo free. /download-video-naruto-vs-pain-full-movie-bahasa-indonesia.html.
/users/ generateduid10.5 (Leapord) and 10.6 (Snow Leapord)# dscl localhost -study /Search/Users/ grep GeneratedUID cut -d15-This should come back a value which seems in the using file format: A66BCB30-2413-422A-A574-Para03108F8AF2STEP 2. EXTRACTING THE HASHESNext, we desire to acquire the SHA1 hásh from the shadów file. For this, we perform the adhering to:# cat /var/db/shadów/hash/A66BCB30-2413-422A-A574-DE03108F8AN2 cut -c169-216Note: Replace the above GUID with the 1 you have got removed from the previous phase.You should have been returned with á SHA1 hash thát looks identical to the using: 33BA7C74C318F5D3EF40EB25E1C42F312ACF96At this stage it should become noted that OS X provides the capability to shop Screen NT ánd LANMAN hash répresentations. This will only happen if SMB/CIFS document sharing has been turned on. To remove these passwords from the shadow document, type the foIlowing:NT:cat /vár/db/shadow/hásh/A66BCB30-2413-422A-A574-DE03108F8AN2 lower -c1-32LANMAN:cat /var/db/shadow/hash/A66BCB30-2413-422A-A574-DE03108F8AN2 lower -chemical33-64STEP 3.
Breaking THE PASSWORDAt this stage we are usually prepared to crack the Operating-system X security passwords. To simplify this stage, I have created a simple python script that can end up being. To make use of this screenplay, simply duplicate and paste the material into a file (osxcrack.py) and kind:#python osxcrack.py bobNote: 'chad' is definitely the username whosé password we need to crack.This technique is fine if you are usually only fascinating in breaking security passwords from a regional system.
If, nevertheless, you have got taken a hash from a remote control system, or would prefer a even more acquainted password cracking utility, then can also be utilized for this phase. In purchase for Mark to work, Tom will require to become patched with the 'Jumbo Repair' - enabling SHA1 passwords (known to as XSHA in David) to be damaged.
The repair can become downloaded from the following locations:.As soon as we have download/patched John, the extracted hásh and username shouId become positioned in a text message document. For this illustration I possess included the username ‘bob' and bob's hash (that I attained in STEP 2) into a document known as sha1.txt. The file has the following format:bob:33BA7C74C318F5D3EF40EB25E1C42F312ACF96We can after that use David the crack the password:#./bob sha1.txtIf Tom is successful in identifying the hash, the pursuing information will become shown:”Loaded 1 password hash (Macintosh OS Back button 10.4+ salted SHA1 32/64)”A productive cracking try will appear as follows:passwórd (bob)guesses: 1 period: 0:00:00:00 100% (2) c/s: 153000 trying: passwordAdditional Resources.